On 27th July, Mackenzie Jackson and Eric Fourrier hosted a live webinar on Intrusion detection in DevOps environments with AWS canary tokens. They also talked about the launch of ggcanary, or the GitGuardian Canary Tokens, and an awesome demo. It was inspiring to hear about their journey and what they do, so I decided to sum up what I learned over the course of the seminar.
Here are some of the important links that you might need to understand things clearly:
Every stage of the DevOps pipeline is now an attractive target for attackers. Starting from Planning (Jira, slack, Figma, etc.) to code (vs code, JetBrains, etc.), testing (Jenkins, GitLab etc.), package (Docker hub, nexus etc.), security (synk, vercode, etc) to deployment (chef, ansible, etc) and monitoring (grafna, datadog, etc). To understand thing in detail you need to know what supply chain attack is
Supply chain attacks: A supply chain attack, also called a value-chain or third-party attack, occurs when someone infiltrates your system through an outside partner or provider with access to your systems and data. This has dramatically changed the attack surface of the typical enterprise in the past few years, with more suppliers and service providers touching sensitive data than ever before.
Example of supply chain attack: Codecov breach
Codecov customers’ environment variables were sent to a remote server by sophisticated attackers who exploited a mistake with the way Codecov builds docker images. According to other disclosures, the attackers were able to access private git repositories using the git credentials in the CI environment, and then exploit the secrets and data contained there. You can read more about it here: link
Detecting intrusion in the supply chain
It can be done in several ways. Most popular ones are
-
network-based: A network-based intrusion detection system (NIDS) detects malicious traffic on a network. NIDS usually requires promiscuous network access in order to analyze all traffic, including all unicast traffic.
-
host-based: A host-based intrusion detection system is an intrusion detection system that is capable of monitoring and analyzing the internals of a computing system as well as the network packets on its network interfaces, similar to the way a network-based intrusion detection system operates.
-
canary (or honey) token based: A canary token is a file, URL, API key, or other resources that are monitored for access. Once the resource has been accessed, an alert is triggered notifying the object owner of said access. Typically, canary tokens are used within an environment to help defenders identify a compromised system or a resource that should not be accessed. At the point of file access, an e-mail or some other type of notification can be triggered to notify the system owner, and then appropriate responses can occur.
How to detect compromised developer and DevOps environments with canary tokens?
Canary tokens can be created and deployed in your code repositories, CI/CD pipelines, project management, and ticketing systems like Jira or even instant messaging tools like Slack. When triggered, canary tokens can help alert you of an intrusion in your developer environments.
ggcanary tokens
AWS credentials are used as honey tokens in ggcanary, an intrusion detection system by GitGuardian. Today’s software factories are complex and there are a lot of DevOps tools that make it difficult to detect compromises. With ggcanary, we believe security and detection engineers can increase their chances of catching intrusion in this part of their organization by deliberately exposing AWS credentials.
key features of ggcanary tokens
- use terraform to manage canary token infrastructure
- deploy up to 5000 canary tokens
- track every action on AWS CloudTrail logs
- get real-time email alerts if tokens are triggered
- ggcanary leverages current techs like Terraform and AWS
Why use aws secrets as canary tokens?
- AWS secret keys are among the top most leaked secrets
- popular opensource secret scanner support AWS keys
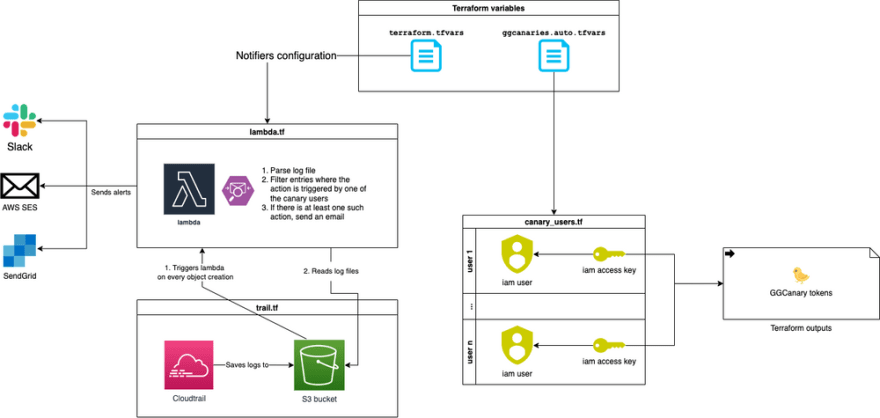
How does it work under the hood?
This simple architectural diagram explains the data flow. Visit the GitHub repo
for a deeper dive into the code.
Conclusion
Ggcanary is the easiest solution for security teams to create and manage AWS honey tokens on a large scale. It is an innovative and brilliant approach to securing software supply chains like Source Control Management (SCM) systems, Continuous Integration and Continuous Deployment (CI/CD) pipelines, and software artifact registries as entry points.
Overall the webinar was an extremely informative event that will undoubtedly influence my view on development from now on. The speaker was very articulate and knowledgeable while remaining interesting throughout which maintained the audience’s attention. Time well spent!