I rely on Thunderbird for my email communication. That is why I generate my OpenPGP keys with their key manager, not through the gpg itself.
This morning, I set up my Web Key Directory (WKD) so anyone with an email client that supports this can auto-discover my public OpenPGP key without needing to look at any key server or rely on information from my website.
Pre-requirements:
- You have already generated a key-pair using Thunderbird
- You own the domain name of the email. You would need that later to upload the WKD files.
- Apache is running on my server to serve the files. (If you are using another server, you easily could find the instructions for the last part)
Thunderbird
Since Thunderbird is using its keychain, there is something else that I need to do.
Here are the steps.
- Open Tools> OpenPGP Key Manager
- Select the Name of the key you would like to use.
- Click on the “File” menu and then to “Backup Secret Key(s) to file.”
- A new dialogue will open. Select the location where you want to store the file.
- Then, you will need to set the protection password for the key. Remember it.
- Now, you can close Thunderbird and open your GPG command line interface.
GPG
I will use Fedora Linux instructions, but I think most commands are the same cross-system.
1: Import the key that you just exported with the following command:
gpg --import [name of the exported file. asc]
2: Then validate that the import happened
gpg --list-keys
You should be able to see something like this:
[bogo@fedora ~]$ gpg --list-keys
/home/bogo/.gnupg/pubring.kbx
pub ed25519 2024-01-19 [SC] [expires: 2027-01-18]
1128C8F2BBD80CA82FE317AF9F03DC07BCECFE7A
uid [ unknown] Bogomil Shopov
sub cv25519 2024-01-19 [E] [expires: 2027-01-18]
3: Let’s generate the file you would need to upload later to your web server containing the information about your public key that will be auto-discovered.
gpg --with-wkd-hash --fingerprint [your email address here]
In my case is:
[bogo@fedora ~]$ gpg --with-wkd-hash --fingerprint bogomil@bogomil.info
pub ed25519 2024-01-19 [SC] [expires: 2027-01-18]
1128 C8F2 BBD8 0CA8 2FE3 17AF 9F03 DC07 BCEC FE7A
uid [ unknown] Bogomil Shopov
4b5a97n4drfkijffzpxjyobkb3h6dfxy@bogomil.info
sub cv25519 2024-01-19 [E] [expires: 2027-01-18]
You need to copy this part of the uid and then:
gpg --export bogomil@bogomil.info >[put this part here]
In my case it would be
gpg --export bogomil@bogomil.info > b5a97n4drfkijffzpxjyobkb3h6dfxy
Website
Now we need to move to your website. You must have access to the leading directory of it. For most hosting providers, this is the www directory or the public_html shortcut that leads to the same one.
- Create there a directory called .well-known (mind the dot). There is a big chance to be already created for another purpose.
- Then, in this folder, create a new one called “openpgpkey”.
- In the newly created folder add an empty file called “policy”
- And another folder in “openpgpkey”, called “hu” (s2)
- In the “hu” folder create .htaccess file (mind the dot) and add the following content there :
ForceType application/octet-stream
Header always set Access-Control-Allow-Origin "*"
- Then upload the gpg-generated file to the “hu” directory
Validation
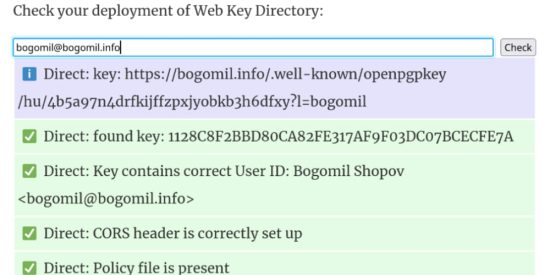
To see whether you did a great job, enter your email address using the following validator. The results should be similar to mine.
Now, every service that discovers public keys via WKD can get yours by using your email address while composing a new message.
Thunderbird and WKD
Natively, Thunderbird doesn’t support auto-discovery with WKD. Most of my peers I communicate with use webmail clients or other software that supports that, so I did this for them, and then when I receive their e-mail with their key attached, I can add it to my trust list.
You are one step more protected! Good job!