Introduction
This challenge is fairly simple. What we mainly needed to do was figure out the filetype of the rootfs file using the file command. After that, we just needed to do some basic research on how to extract the data from a SquashFS file (unsquashfs). Using grep on the entire extracted filesystem, we were able to locate the file that the flag was in.
First Impressions
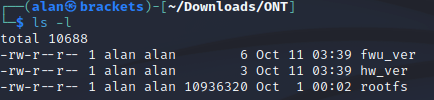
After downloading the challenge file and unzipping the contents, we see three files listed as so: fwu_ver, hw_ver, and rootfs.
Upon a little research, we can see that the file named rootfs is an abbreviation for root file system.
Using ls paired with the -l flag, we can see more information about the three files. What I’m mainly interested in is the size of each file:
We can see that the the file rootfs is by far the biggest, and this is probably due to the fact that it is a root file system.
We are first going to inspect the rootfs file. Since there are no visible extensions for the file, we are going to use the file command to gain more information about the type of file it is, as well as some basic information regarding the file’s contents.
From this, we can see that it is a Squashfs filesystem that has been compressed.
SquashFS
After some basic research, it was found that SquashFS is a compressed read-only file system.
In order to restore the filesystem to a more readable format, we need to extract the filesystem from rootfs.
After some more research, it was found that we can do this using the unsquashfs command. For this to work however, we need to run the command as a super user. This can be accomplished with the sudo command plus the command we wish to execute.
After we successfully run the command, we are given a new directory called squashfs-root containing the extracted filesystem from rootfs.
After changing directories to the extracted filesystem using cd…
GREP
I figured to find the flag, I would just use the grep command to find the regular expression HTB, since that is what HackTheBox flags start with. By pairing the grep command with -l (list files that contain a match) and -r (recursive mode to traverse directories), I searched the entire filesystem for an expression that contained HTB, which would be the starting characters for the challenge’s flag.
This yielded three files with a match: bin/ip, bin/tc, and etc/config_default.xml. Using cat on the first two yielded nothing but machine code that is unreadable. The third one (etc/config_default.xml), however, was in plaintext.
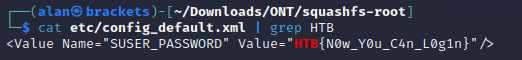
I then decided to use grep again for HTB by piping the output of cat on the config_default.xml.
This yielded the flag we were looking for, as well as valuable login information.