Browsing Tag
security
212 posts
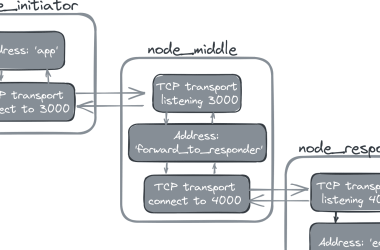
Create End-to-End Channels in Rust with Ockam Routing
build-trust / ockam Orchestrate end-to-end encryption, cryptographic identities, mutual authentication, and authorization policies between distributed applications – at…
True Secrets Auto Rotation with ESO and Vault
Requirements A Kubernetes cluster that you can use (kind, minikube, something managed) and kubectl to connect to it…
Designing the user experience of passkeys on Google accounts
Posted by Court Jacinic, Senior UX Writer, Mitchell Galavan, Interaction Designer, and Silvia Convento, User Experience Researcher This…
Building Trust in a Trustless World: Decentralized Applications Unveiled
In this chapter, we’ll explore decentralized applications, or DApps. They were born from Ethereum’s vision of reinventing the…
Ethereum’s Oracles: Unleashing Trustless Wisdom from Beyond the Blockchain
In this chapter, we’ll explore oracles in Ethereum. Oracles are systems that link Ethereum smart contracts with external…
What is HTTPS and how does it work?
Have you ever wondered how websites communicate with a web browser and request data to the server to…
Denylists and Invaliding user access
This articles discusses and reviews the different ways to invalidate a user’s access and revoke their tokens. It…
Unveiling the Power of AI in Software Security at DevSecCon
Sometimes the very best conferences are online and even free to attend, like DevSecCon from @snyk. Attending such…
Understanding Security Vulnerabilities: A First Step in Preventing Attacks
When I was a teenager, our local telephone company introduced a new service – the premium phone calls…
Securing ChatGPT at Work: Preventing Content Leaks 🔒
ChatGPT is a powerful tool, but it can also be risky if misused in a business environment. Several…