Content
1. Network Penetration Testing – A Quick Overview
2. Why Should Digital Businesses Consider Network Penetration Testing?
3. Steps Involved in Network Penetration Testing
4. Types of Network Penetration Testing
5. Best Network Penetration Testing Tools in 2023
7. Conclusion
8. How can TestingXperts Help with Network Penetration Testing?
Network Penetration Testing – A Quick Overview

Penetration testing, or pen testing, involves simulating cyberattacks against the systems to help identify any vulnerabilities that could be potentially exploited. Network penetration tests use various hacking techniques to identify security vulnerabilities in applications or networks. These tests use real methods and approaches that a hacker could use to access the system, providing critical information about the security of a network.
Penetration testing, in general, is the practice of attempting to breach a computer system or network to discover security flaws. Testers use various methods to gain access to systems, including exploiting vulnerabilities, social engineering and brute force attacks.
Why Should Digital Businesses Consider Network Penetration Testing?
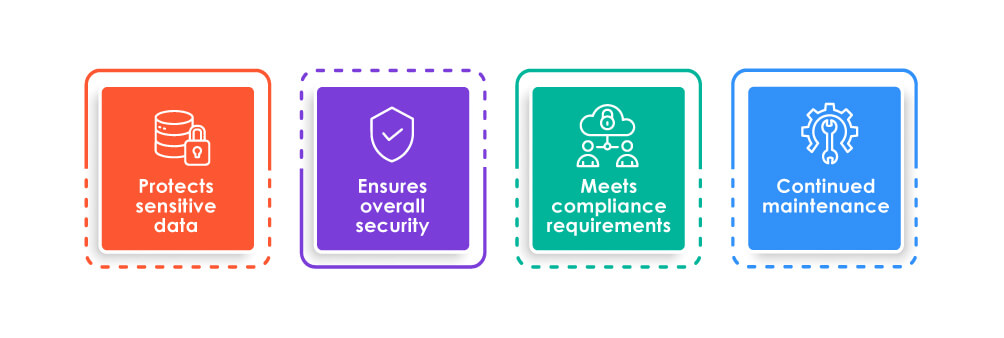
Protects sensitive data
There is no denying the fact that digital businesses must guard themselves against data breaches. Penetration testing often functions like ethical hacks and simulates cyber-attacks as best as possible. A minor glitch can leak sensitive data, affecting customers’ trust, affecting brand value, and also violating industry regulations. Here, a helpful way to determine the level of intrusion is to identify levels of risk that the application is exposed to.
Ensures overall security
Be it the business model, sensitive data, or newly released apps, pen testing ensures that no overlooked flaw compromises the business integrity. Security assessments and website security scans should be a part of any initiative that involves sensitive data. Some examples of such flaws include SQL injections, misconfigured firewalls, outdated software, virus and malware.
Meets compliance requirements
Certain security regulations insist on penetration testing, irrespective of the industry. For example, data security for the payment transactions ensures that such tests help clients protect customers’ sensitive information (PCI DSS).
Continued maintenance
Network pen tests require multiple continuous runs to ensure long-term security. Penetration testers look over the security controls used for the business network, such as firewalls, layered security, encryption processes, etc.
Benefits offered by network penetration testing to digital businesses:
Specifically, the following are ways pen testing helps understand and improve overall security
Understanding network benchmarks
• Testing security controls
• Evaluating security posture
• Identifying security flaws
• Assessing risk
• Addressing and fixing identified network security flaws
• Preventing network and data breaches
• Ensuring network and system security
Steps Involved in Network Penetration Testing
In simplest terms, network pen testing simulates a real-life attack, providing critical information about potential weaknesses hackers could use as entry points to gain access to the network. Ethical hackers use a variety of methods to attempt to compromise the network.
A typical network pen testing approach involves the following steps:
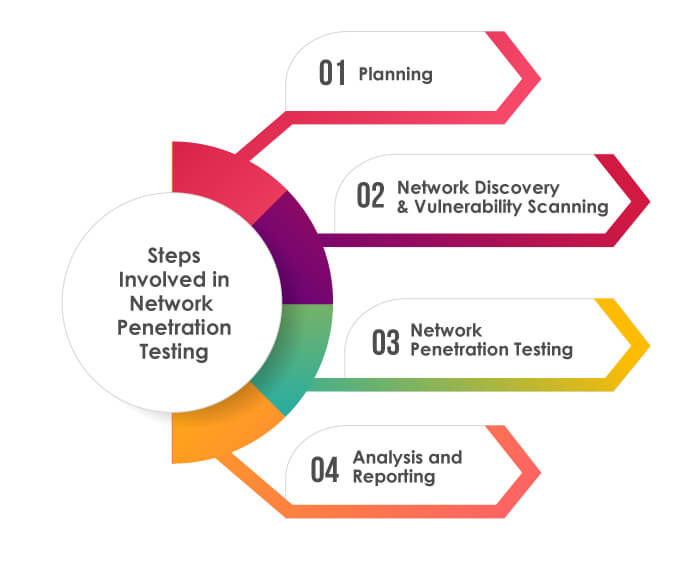
Planning
In the planning phase, ethical hackers discuss the scope and overall aim of the test with critical stakeholders. Testing methods and success metrics are defined in this initial discussion phase. After an introductory overview is decided upon, certified ethical hackers survey all components of the businesses’ network.
Network Discovery & Vulnerability Scanning
In this phase, penetration testers perform TCP and UDP port scanning to identify live hosts on the target network, open ports and services running on the ports. After that, testers perform vulnerability scanning on the discovered hosts and open ports to find potential vulnerabilities.
Network Penetration Testing
After testing the network to understand its behaviour, perform automated scanning validation to manually verify the results from scanning in previous phase. Then, penetration testing is performed where testers try to exploit the network and applications hosted in the network by leveraging misconfigurations and software vulnerabilities such as buffer overflows, injection, brute force attacks, etc.
Analysis and Reporting
After completing testing activities, pen testers will analyse their results and create a report showing their findings. This report will provide actionable insight into vulnerabilities, actual exploitability and the chance for businesses to take necessary remediation action before a real hacker can exploit their system.
Types of Network Penetration Testing
A few different types of network penetration testing can impact the structure and deliverables of the penetration testing methodology described above. Specifically, there are two main categories of network penetration testing:
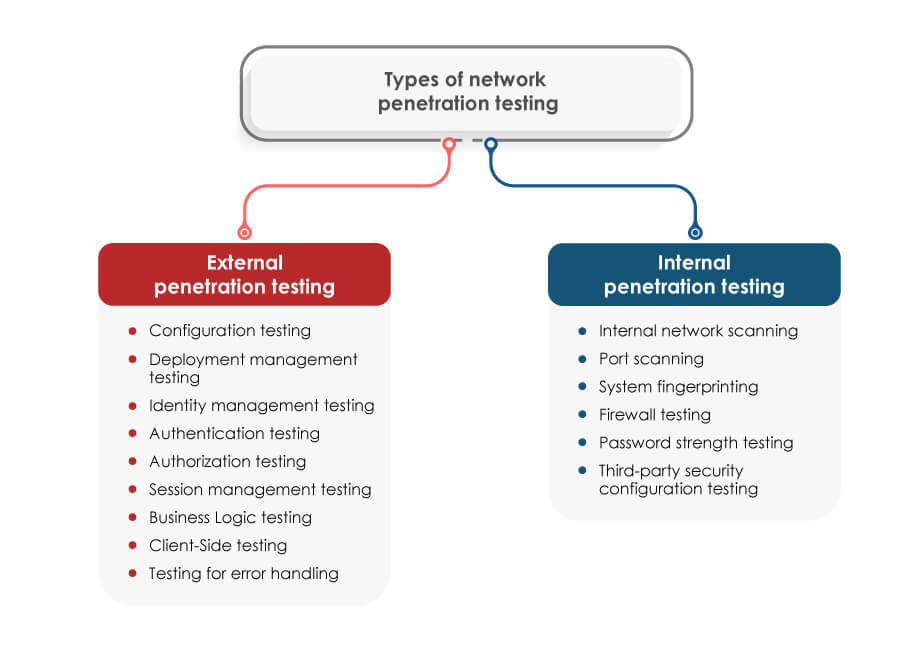
External penetration testing
External penetration testing evaluates the vulnerabilities to analyse the possibility of being attacked by a remote intruder and exploiting the vulnerabilities and information being exposed to outsiders. As a result, the test shows whether the cybersecurity measures implemented by an organisation suffice to secure sensitive data and assesses its potential to safeguard against external attacks.
External penetration tests include:
• Configuration testing
• Deployment management testing
• Identity management testing
• Authentication testing
• Authorization testing
• Session management testing
• Business Logic Testing
• Client-Side Testing
• Testing for error handling
Internal penetration testing
An internal penetration test uses a different way of dealing with the attacks and comes into the picture after an external penetration test is completed. Internal penetration testing aims at identifying what could be accomplished by an intruder who may break into the network and gain unauthorised access. Internal tests reveal that should an attacker gain access equivalent to an insider, or if any malicious internal user tries to break the security, what impact could it have on the disclosure, misuse, alteration, or damage to the confidential information.
Internal penetration tests include:
• Internal network scanning
• Port scanning
• System fingerprinting
• Firewall testing
• Password strength testing
• Third-party security
• configuration testing
Best Network Penetration Testing Tools in 2023

NMAP
Key Features
• Helps map a network by scanning ports, discovering operating systems and creating device inventory
• Easy to navigate
• Easy Wide range of networking features
Metasploit
Key Features
• Used by security professionals to detect systematic vulnerabilities
• Contains portions of fuzzing, anti-forensic and evasion tools
• Currently includes nearly 1677 exploits
WireShark
Key Features
• Capture and analyse network traffic
• Inspect and decrypt protocols
• Capture live data from Ethernet, LAN, USB, etc.
•Export output to XML, PostScript, CSV, or plain text
Nessus
Key Features
• Allows efficient vulnerability assessment
• Accurate identification of vulnerabilities
• Integrates with the rest of the product portfolio
ZAP
Key Features
• Available for Windows, Linux and Mac
• Detects a variety of vulnerabilities within web apps
• Easy to navigate UI
• Supports many pen-testing activities
Indusface WAS
Key Features
• Pause and resume feature
• Enables manual penetration testing
• Checks for malware infection, the reputation of the links on the website and defacement and broken links
• Unlimited POC requests to provide evidence of reported vulnerabilities and remove false positives
Astra
Key Features
• 3000+ tests scanning for CVEs in OWASP top 10, SANS 25
• Testing for ISO 27001, HIPAA, SOC2, GDPR
• Integration with GitLab, GitHub, Slack and Jira
• Zero false positives ensured by manual pen-testers
• Scans progressive web apps and single-page apps
• Scan behind logged-in pages
• Intensive remediation support
Conclusion
A network penetration test is a deep dive into security. It is an effective way to view the application or network security from a hacker’s perspective. Once the security has reached a particular stage, pen testing is essential to a business’s security plan. Network penetration testing provides visibility, confidence and increased security to the network. It improves the network’s security, identifies attack vectors and tests incident response procedures. Network pen testing requires specialised knowledge and skills, so it’s essential to understand the requirements and have professional penetration testing experts perform effective testing to meet the desired security outcomes.
How can TestingXperts Help with Network Penetration Testing?

TestingXperts (Tx) is one of the five largest global pure-play software testing services providers. Tx has been chosen as a trusted QA partner by Fortune clients and ensures superior testing outcomes for its global clientele. We have rich expertise in enabling end-to-end security testing services for global clients across various industry domains like healthcare, telecom, BFSI, retail & eCommerce, etc.
With our domain knowledge and with over a decade of pure play testing experience, the company has been serving the global clientele with high-quality next-gen software testing services to deliver superior solutions to clients.
Our Differentiators:
• Large pool of CEHs (Certified Ethical Hackers).
• Conformance with international standards, including OWASP and OSSTMM.
• Vendor independence coupled with deep expertise in key security technologies.
• The report classifies each vulnerability into appropriate categories along with mitigation strategies.
• Ensuring zero false positives with snapshots of exploitation.
• Complete coverage of regression testing.
• Vulnerability-free application with an iterative strategy for further release.
• Supported Tools: Hp Web Inspect, IBM App Scan, Acunetix, Cenzic Hailstorm, Burp Suite Pro and other open-source tools.
The post Network Penetration Testing – An Informative Guide first appeared on TestingXperts.







Can I say what relief to locate one who really knows what theyre talking about on the web. You certainly understand how to bring a challenge to light and earn it essential. More and more people need to ought to see this and understand why side of your story. I cant think youre not more common because you certainly have the gift.
Remarkably! It is like you read my mind! A person seem to know therefore much relating to this, exactly like you authored it in it or something. We believe which you can do with a few images they are driving the message house a bit, besides that, this is great blog. A exceptional read. I will certainly revisit once more.
This is actually attractive, You’re an exceedingly qualified author. I have signed up with your feed plus expect enjoying the useful write-ups. Furthermore, I’ve shared yuor web blog throughout our internet sites.