“@context”: “https://schema.org”,
“@type”: “FAQPage”,
“mainEntity”: [{
“@type”: “Question”,
“name”: “How Should CISOs Safeguard their Businesses Leveraging Security Testing?”,
“acceptedAnswer”: {
“@type”: “Answer”,
“text”: “With the new normal of WFH, employees should be made to assess, manage, and monitor their network endpoints to build trust in their systems. Employees should leverage Zero Trust Architecture to address the lateral threat network movement within a network by using micro-segmentation and granular perimeters enforcement.”
}
},{
“@type”: “Question”,
“name”: “What is Phishing Attack?”,
“acceptedAnswer”: {
“@type”: “Answer”,
“text”: “This is a common cybercrime seen everywhere today, in which a fraudulent attempt is made through emails to steal an employee’s personal information. These emails appear to come from well-known organizations and other links wherein people fall prey to them and will lose their security access details as they tend to open these emails.”
}
},{
“@type”: “Question”,
“name”: “What is Ransomware Attack?”,
“acceptedAnswer”: {
“@type”: “Answer”,
“text”: “This is a type of malicious attack by cybercriminals observed, as they block the user from accessing their data.”
}
},{
“@type”: “Question”,
“name”: “What is Port Number & Network Footprint Attack?”,
“acceptedAnswer”: {
“@type”: “Answer”,
“text”: “Keeping in mind the remote work concept, many cyber attackers are actively looking to make changes in port numbers and thus attack their web traffic.”
}
}]
}
Content
1. Major Security Threats on IT Security During Pandemic
2. How Should CISOs Safeguard their Businesses with Security Testing?
2.1 Proper Monitoring of Endpoints
2.2 Identify Threats & Vulnerabilities with Security Testing
2.3 Incorporate Secure Video Conferencing
2.4 Intelligent Identify and Access Management
2.5 Increased Bandwidth Allocation
2.6 Ensure Proper Configuration of Personal Devices
2.7 Multifactor Authentication (MFA) Bypass
2.8 Split Versus Full Tunnel VPN Visibility
3.Conclusion
Undoubtedly, the coronavirus pandemic has caused a massive crisis for mankind and made us all reconsider our perception of this new world. This COVID-19 has led to an unexpected change in human life with a series of lockdowns and social distancing norms. Along with these new norms, especially the IT world has been dragged into the adoption of the new normal – ‘WFH.’
The pandemic has forced masses to work remotely and this new alignment of work adjustment has expanded the security threat landscape. As employees try to adjust to the WFH, still it underlies many security risks and mandates the IT team’s support that is much needed to make this WFH process a success.
Moreover, along with WFH normal, VPN, remote connections, multi-factor authentication, and video conferencing tools have become an integral part of this newly formed work culture. The World Economic Forum stated that the world is entering a volatile and unstable new phase. Scientists are increasingly confident that the COVID-19 pandemic threat will persist, possibly for years.
Another recent survey of 100 CIOs in North America conducted by Hitachi ID and social research firm Pulse state that, 95% of the respondents admitted that their IT teams have been bogged down by remote working efficiencies during the COVID-19 crisis. Among the challenges, employee password lockouts were the top issue cited by 71% of those surveyed. Specifically, IT support is being hit with more requests for sign-in assistance on the part of employees.
Evidently, today companies grapple with the pandemic situation as they continue to face security threats by hackers and other cyber attackers during this current situation. Organizations are unable to balance their business as usual processes.
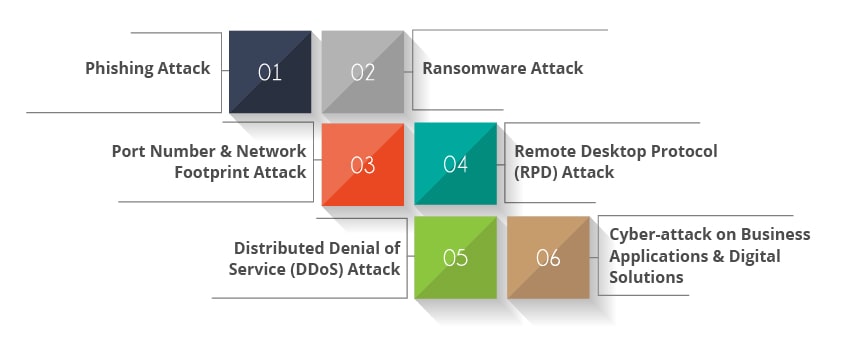
Major Security Threats on IT Security During Pandemic
Phishing Attack:
This is a common cybercrime seen everywhere today, in which a fraudulent attempt is made through emails to steal an employee’s personal information. These emails appear to come from well-known organizations and other links wherein people fall prey to them and will lose their security access details as they tend to open these emails.
According to a Cyber Defence Centre (CDC) report, employees are the new perimeter for security. Attackers too have not been left untouched by the pandemic and we’ve seen a sharp rise in Phishing scams in the last few months. From our CDC, our team has observed that attacks which were Covid-19 themed (including phishing and brute force) rose as much as 100%.
In another survey by cyber security firm Check Point, it has been stated that “Phishing attempts (55 percent) and websites claiming helpful information on coronavirus (32 percent) have emerged as the leading threats to the organizations, the respondents said.
In phishing attacks, a bad actor steals sensitive information by tricking people to open an email, instant message, or text message containing malicious links or attachments.” The findings showed that the rapid changes to enterprise working practices, and broader concerns about the pandemic, are both being exploited by cybercriminals as they step up their attacks, generating a raft of new challenges for security professionals.
Ransomware Attack:
This is a type of malicious attack by cybercriminals observed, as they block the user from accessing their data. This attack process consists of encrypting the files in their systems and deliberately adds extensions to the attacked data and holds the user as a hostage and demands a ransom to be paid. Interestingly, most ransomware gangs demand payment in bitcoins, the most high-profile cryptocurrency, although some began shifting their demands to other currencies as bitcoin’s popularity made its value more unpredictable.
According to a report by Cybersecurity Ventures, it has been stated that over the years, ransomware has grown from curiosity and an annoyance to a major crisis deeply twisted together with top-secret spy agencies. Ransomware cyberattacks are big business, so big in fact, that research anticipates a business is attacked by a cybercriminal every 11 seconds and damage costs from these attacks will hit around $20 billion by 2021.
Port Number & Network Footprint Attack:
Keeping in mind the remote work concept, many cyber attackers are actively looking to make changes in port numbers and thus attack their web traffic.
According to a Tech Target report, hackers are watching for changes in network footprints and exploring how they can exploit security gaps. Chief Information Security Officers (CISOs) need to be aware that any change on the networks should be essentially watched as they occur.
There are certain instances of VPN attacks seen during these days, as attackers closely see that a new VPN connection has been established and thus, try to find credentials of that particular organization on the dark web and try to attack it.
Remote Desktop Protocol (RPD) Attack:
As employees continue to work remotely, there is an increase in the number of systems with open RDP that can be potentially targeted. This RDP provides network access for a remote user over an encrypted channel.
The IT teams and network administrators use RDP to diagnose network issues, essentially use it for logging into servers, and also perform other remote actions. Specifically, cyber attackers use misconfigured RDP points to gain access to various networks.
Distributed Denial of Service (DDoS) Attack:
Downtime from these DDoS attacks is also reported by many organizations and is detrimental when seen with a large remote workforce. At times, there might be an unintentional DDoS attack when numerous users try to access the services at the same time.
Cyber-attack on Business Applications & Digital Solutions:
Today’s cyber-attacks have been ever-increasing and any sort of security breach adversely affects either applications or networks. These cyber-attacks might lead to the loss of customer data followed by loss of brand loyalty and sometimes might also lead to legal complications.
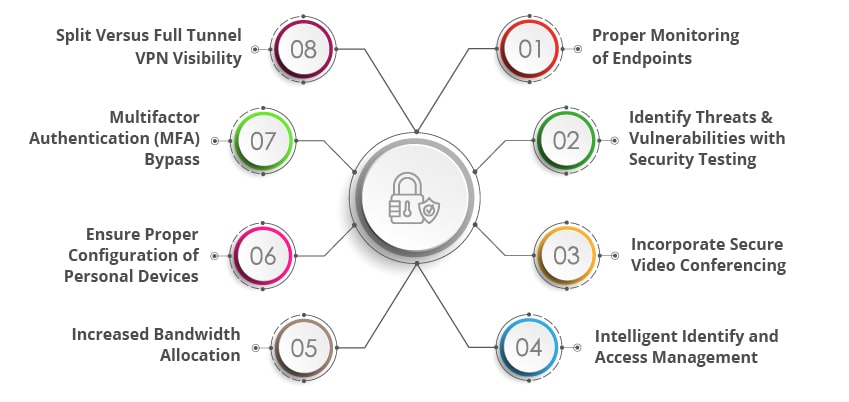
How Should CISOs Safeguard their Businesses with Security Testing?
Proper Monitoring of Endpoints:
With the new normal of WFH, employees should be made to assess, manage, and monitor their network endpoints to build trust in their systems. Employees should leverage Zero Trust Architecture to address the lateral threat network movement within a network by using micro-segmentation and granular perimeters enforcement.
Identify Threats & Vulnerabilities with Security Testing:
Organizations should embrace end-to-end security testing and application security testing leveraging security testing companies to protect their websites, apps and digital applications from phishing and ransomware attacks. Organizations should proactively detect vulnerabilities within the network to understand internet exposure and get to know the probable susceptibility to phishing attacks.
Incorporate Secure Video Conferencing:
Video conferences have become the new means of communication for remote employees working globally. It is important to use private and password protected meeting links to ensure security. New meeting Id’s and passwords should be generated to use a fresh with each session of the meeting in order to protect their sessions.
Intelligent Identify and Access Management:
It is essential for organizations to manage identities on the go when there is a complex ecosystem of stakeholders operating globally. Effective, comprehensive and automated identity management solutions ensure that only the right people have the necessary access to critical or confidential data, computers, networks, and other resources.
Increased Bandwidth Allocation:
In order to handle DDoS attacks, organizations should have increased bandwidth allocations ready, and it is important to temporarily disable unused services to allow more bandwidth. Employees should be discouraged from using live streaming services through a VPN.
Ensure Proper Configuration of Personal Devices:
It is essential that all employees have been set up with new VPNs or virtual desktops. They should ensure proper anti-virus to be installed in their systems even within their personal devices. When an employee downloads a VPN on to their laptop that has already been compromised with some malicious attack then they could easily spread the malware into the organization’s corporate network and hence care should be taken.
Multifactor Authentication (MFA) Bypass:
Organizations should implement MFA to reduce credential spraying attacks. Employees should be trained to identify and report unauthorized push notifications. It is essential for organizations to evaluate the risk tolerance even before taking up the MFA implementation methods.
Split Versus Full Tunnel VPN Visibility:
In case there are numerous remote workers available, then it is preferred for organizations to move from a full tunnel VPN configuration towards Split Tunneling. Full tunnelling VPN helps to see that all traffic traverses the VPN allowing web proxies to filter traffic and security teams will be able to identify unauthorized activity if any. While Split tunnelling may reduce this visibility unless proper endpoint agents are installed to ensure proper control.
Conclusion
The COVID-19 pandemic has invaded the mankind in different ways and enforced social distancing and made a mandate of new normal of WFH for all IT employees. This sort of new normal has led way to some security compromise and made it easy for hackers to attack employee systems and also IT networks.
Hence, in order to protect your business and the new normal of WFH, it is essential to leverage security testing services to ensure proper protection from threats and vulnerabilities. In addition, businesses should also follow password protection, Split or Full tunnel VPN and other methods of security measures to make sure remote workforce is secure and protected from any sort of vulnerabilities either at the system-level or at the network-level.
Talk to our Security testing experts and understand how we can help your business avoid such cyber threats
Recommended Reading Blogs
1. Top Cyber Security Trends 2020
2. How to Mitigate DDoS Attacks?
3. What is Cryptojacking?
4. How cyber Security Testing Can Help?
5. 7 Crucial Activities to Test the Security of your Mobile Applications?
6. Significance of Application Security Testing in Preventing Cyber Attacks?
Related Queries on It Threats and Cyber Attacks
Q1. What are the types of cyber attacks?
Ans. The most common forms of cyber-attacks are Malware, Phishing, SQL Injection attack, DDos attack, Cross-Site Scripting (XSS)
Q2. How cyber attacks can be reduced?
Ans. Security Testing is taken up to identify threats and vulnerabilities in the system by proper monitoring of endpoints, identify threats & vulnerabilities with security testing, read more.
Q3. Why cyber security is needed?
Ans. Cyber Security testing ensures that all IT systems in the organization are free from all kinds of vulnerabilities and weaknesses.
The post IT Security Measures CISOs Must Take During and Post Pandemic first appeared on TestingXperts.